Infrastructure as Code Testing Explained: From Code to CI/CD Pipelines

You would never deploy application code without tests, so why ship untested infrastructure? This is the shift in mindset behind Infrastructure as Code testing. The use of Infrastructure as Code (IaC) revolutionized how teams handle their servers, networks, and cloud resources. However, the speed and automation that make IaC appealing can lead to production outages due to minor errors.
The problem is that untested infrastructure scripts have the potential to create security vulnerabilities, cause downtime, or disrupt CI/CD processes. Infrastructure as Code testing is a safety net that introduces quality by ensuring infrastructure changes can be validated in advance, prior to making them reside in production, providing assurance to QA and DevOps teams alike.
But before we start talking about how IaC integrates with CI/CD pipelines, let’s take a step back and ask ourselves the most fundamental question: what is Infrastructure as Code?
- What is Infrastructure as Code?
- Understanding Infrastructure as Code Testing
- Infrastructure as Code Testing in CI/CD Pipelines
- How to Implement IaC Testing in CI/CD Pipelines
- IaC Testing Best Practices
- Common Challenges in Infrastructure as Code Testing
- Infrastructure as Code Examples in Testing
- Conclusion
What is Infrastructure as Code?
At its core, Infrastructure as Code (IaC) is the practice of managing and provisioning infrastructure using machine-readable code instead of manual configuration. Instead of clicking through a cloud dashboard, you define infrastructure in scripts using tools like Terraform, Ansible, or AWS CloudFormation.
It’s infrastructure expressed as code files that can be versioned, reviewed, and automated just like application code.
Benefits of Infrastructure as Code:
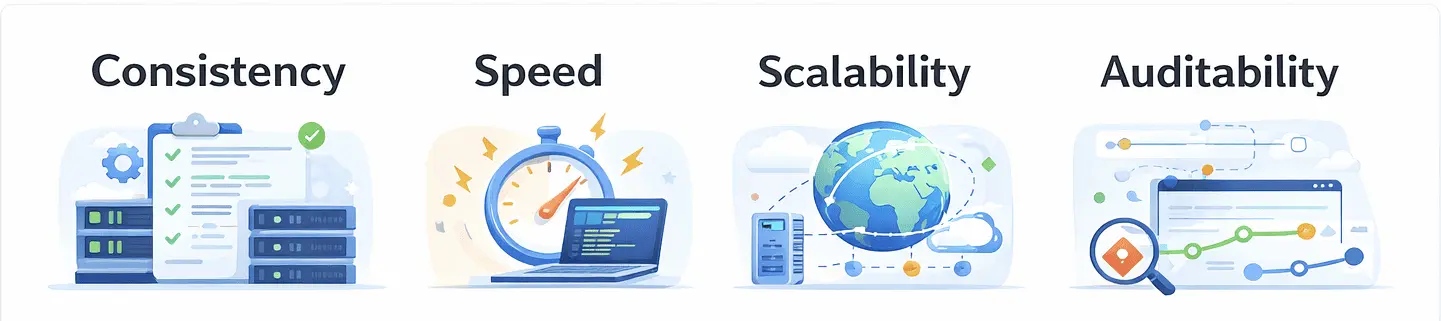
- Consistency: Every deployment uses the same definitions, reducing “it works on my machine” issues.
- Speed: Environments can be spun up in minutes, not weeks.
- Scalability: Teams can replicate environments across regions effortlessly.
- Auditability: Changes are logged and traceable through Git history.
But here’s the catch: IaC isn’t inherently safe. Scripts can have misconfigurations, overlooked dependencies, or security gaps. That’s why Infrastructure as Code testing is a necessary extension.
SUGGESTED READ - Scalable CI/CD solutions with Agile DevOps
Understanding Infrastructure as Code Testing
Infrastructure as Code testing is the practice of validating IaC scripts to ensure they do what’s intended, and nothing else. Just as we run unit tests on application code, we need validation for infrastructure definitions.
Why it matters:
- IaC vs IaC Testing: While IaC provides speed, IaC testing ensures reliability and security.
- Types of IaC Testing:
- Unit testing modules: Verify individual Terraform or Ansible components.
- Static analysis: Detect misconfigurations before deployment.
- Integration tests: Confirm infrastructure interacts correctly with apps.
- Security checks: Scan for policy violations, open ports, or weak configurations.
Think of it as applying the test automation pyramid to infrastructure. Regression, functional, and security testing all apply, just at a different layer.
Infrastructure as Code Testing in CI/CD Pipelines
So where does IaC testing sit in modern pipelines?
What is IaC in CI/CD?
It’s about embedding infrastructure validation into CI/CD pipelines for infrastructure-as-code delivery. Just like app code, infrastructure scripts should move through build → test → deploy stages.
A typical IaC pipeline includes:
- Code commit: Infrastructure definitions stored in Git.
- Build/Plan: Terraform plan or Ansible dry-run to preview changes.
- Testing: Static checks, unit tests, and policy validation.
- Deployment: Approved code pushes to staging or production.
Example: A Terraform script defines a new VPC. The CI/CD pipeline first runs syntax validation, then policy checks (ensuring no open S3 buckets), before deploying. Without this pipeline, errors could slip directly into production.
How to Implement IaC Testing in CI/CD Pipelines?
Here’s a practical playbook for teams asking: how to implement IaC testing in CI/CD pipelines?
1. Lint & Syntax Tests
- Catch formatting issues early using tools like tflint or ansible-lint.
2. Unit Testing
- Test Terraform modules or Ansible roles in isolation. Example: verify a VPC module creates the correct CIDR range.
3. Integration Tests
- Deploy infra into a sandbox and validate app compatibility.
4. IaC Security Testing
- Use tools like tfsec, Checkov, or OPA for policy-as-code enforcement.
- This is where IaC security testing becomes part of SecDevOps.
5. Shift-left Infrastructure Tests
- Run tests as part of pre-commit hooks or pull requests.
6. Pipeline Automation
- Integrate IaC testing into Jenkins, GitHub Actions, or GitLab CI.
IaC Testing Best Practices
Another overlooked best practice is treating infrastructure tests as living assets. Just like application code evolves, your IaC test cases should evolve with new modules, services, and compliance requirements. Teams that “set and forget” often find their tests outdated within months.
It’s also worth building observability into IaC pipelines. Don’t just run tests, track metrics such as test flakiness, provisioning times, and rollback success rates. These insights reveal whether your infrastructure is reliable over time or prone to hidden bottlenecks.
Finally, embed IaC testing into peer review workflows. Pull requests should include automated test results so reviewers can validate both functionality and infrastructure stability at the same time. This tightens feedback loops and builds confidence in every merge.
Now that you’ve got the mechanics, let’s talk about IaC best practices for testing:
- Automate regression testing for frequent infra changes.
- Keep test suites lightweight so pipelines stay fast.
- Isolate environments to avoid conflicts between test runs.
- Test rollback and recovery, don’t just test creation, test destruction too.
- Embed testing in DevOps workflows for consistency.
- Security-first mindset: never deploy without automated security checks.
This is where the concept of infrastructure as code DevOps really shines, testing becomes part of the culture, not a bottleneck.
SUGGESTED READ - Best practices for production testing
Common Challenges in Infrastructure as Code Testing
Let’s face it: what are the challenges in Infrastructure as Code testing?
- Complexity: Distributed infrastructure is harder to validate than single apps.
- Skill gaps: Few QA engineers specialize in IaC.
- False positives: Security tools can flag harmless configs.
- Environment costs: Spinning up test infra can be expensive.
- Pipeline slowdowns: Heavy infra tests can delay deployments.
The solution? Automation, policy-as-code, and unified DevOps + QA collaboration.
Another challenge often overlooked is cultural resistance. Teams comfortable with manual infrastructure setup may resist adopting Infrastructure as Code testing, slowing transformation. There’s also the risk of tool sprawl, as organizations spin up multiple IaC testing tools without standardization, leading to inconsistent practices and wasted effort. Security teams sometimes join the party late, which means vulnerabilities slip past early testing stages.
Finally, compliance adds another layer of complexity. Financial, healthcare, and government workloads often require auditable evidence of every infrastructure change, making automated test reporting non-negotiable. Without structured IaC testing, these organizations face failed audits, downtime, and regulatory penalties.
Infrastructure as Code Examples in Testing
Examples help make this real.
- Terraform Example: A test validates whether an S3 bucket is encrypted by default.
- Ansible Example: A role is tested for idempotency (running twice produces no changes).
- CI/CD Example: A pipeline fails a deployment if security scans detect public exposure of ports.
These infrastructure as code examples show how even small tests prevent large-scale outages.
Conclusion
Infrastructure as Code testing is not optional, but rather a necessity. It is not safe to leave untested infrastructure scripts unattended. When organizations scale DevSecOps and cloud-native delivery, such scripts are a huge risk.
The advantages of Infrastructure as Code are evident: rapid, scalable, and reliable. However, that can also introduce fragility without testing. By embedding IaC tests in CI/CD the safety, security, and predictability of infrastructure evolution is assured.
Automation, AI, and security-first IaC pipelines all feature heavily in the future. QA leaders who invest today will save outages tomorrow.
👉 Learn how ACCELQ test automation covers native AI-powered quality practices for applications, APIs, and infrastructure pipelines, unifying both DevOps and IaC testing in a single intelligent workflow.
Balbodh Jha
Associate Director Product Engineering
Balbodh is a passionate enthusiast of Test Automation, constantly seeking opportunities to tackle real-world challenges in this field. He possesses an insatiable curiosity for engaging in discussions on testing-related topics and crafting solutions to address them. He has a wealth of experience in establishing Test Centers of Excellence (TCoE) for a diverse range of clients he has collaborated with.
You Might Also Like:
 Agile Testing Trends Every QA Engineer Should Watch Closely
Agile Testing Trends Every QA Engineer Should Watch Closely
Agile Testing Trends Every QA Engineer Should Watch Closely
 What Is Regression Testing In Agile?
What Is Regression Testing In Agile?
What Is Regression Testing In Agile?
 Top 10 Salesforce DevOps Tools
Top 10 Salesforce DevOps Tools